Monitor
Advise
Influence
argon.africa
Snapshot
The Nigerian intelligence community's counterterrorism operations have shifted from reactive raids to systematic leadership disruption.
Sources reported Ansaru fighters are shifting towards Jihadist groups in the NorthEast.
By combining open-source intelligence, human intelligence, and covert operations, security agencies are dismantling militant leadership structures, disrupting financing networks, and exploiting intelligence in ways that are reshaping the battlefield.
Nigeria's intelligence community has quietly executed some of its most consequential counterterrorism operations in years. Through coordinated, low-visibility actions, the Department of State Services (DSS) and the Office of the National Security Adviser (ONSA) have shifted the fight from reactive raids to systematic leadership disruption, a doctrine designed to fracture command networks before they regenerate.
The arrests of Mahmud Muhammad Usman (Abu Bara'a) and Mahmud al-Nigeri (also known as Abubakar Abba/Mahmuda) are the headline wins. Both men were on Nigeria's most-wanted list, captured in a multi-agency operation conducted between May and July 2025 but only revealed later, after weeks of intelligence exploitation. In court, Usman pleaded guilty to illegal mining used to finance terrorism and received 15 years, an important conviction that attacks not just militants in the field but the financial arteries that keep insurgency alive.
What distinguishes this new wave of operations is the intelligence cycle behind them. Arrests are increasingly held back from public view while agencies work their leads: device forensics are mined for contacts and communications; Human intelligence (HUMINT) sources are activated to track facilitators; Open source intelligence (OSINT) monitoring helps corroborate movements and supply lines; and cross-border intelligence liaison maps logistics networks that extend into Niger and Benin. Only once that exploitation window closes are arrests confirmed in the media.
The same rhythm played out in the Southeast with the capture of IPOB/ESN commander "Gentle de Yahoo." He was held for weeks before authorities disclosed the operation, allowing security services to roll up associated cells. The same pattern emerged with Ansaru, where sources reported the covert arrest of Abu Ikiriam, a senior figure within the group, was withheld from media disclosure to maximize intelligence gains. Together, these cases illustrates how the "capture, exploit, then announce" doctrine is quietly becoming a hallmark of Nigeria's counterterrorism playbook.
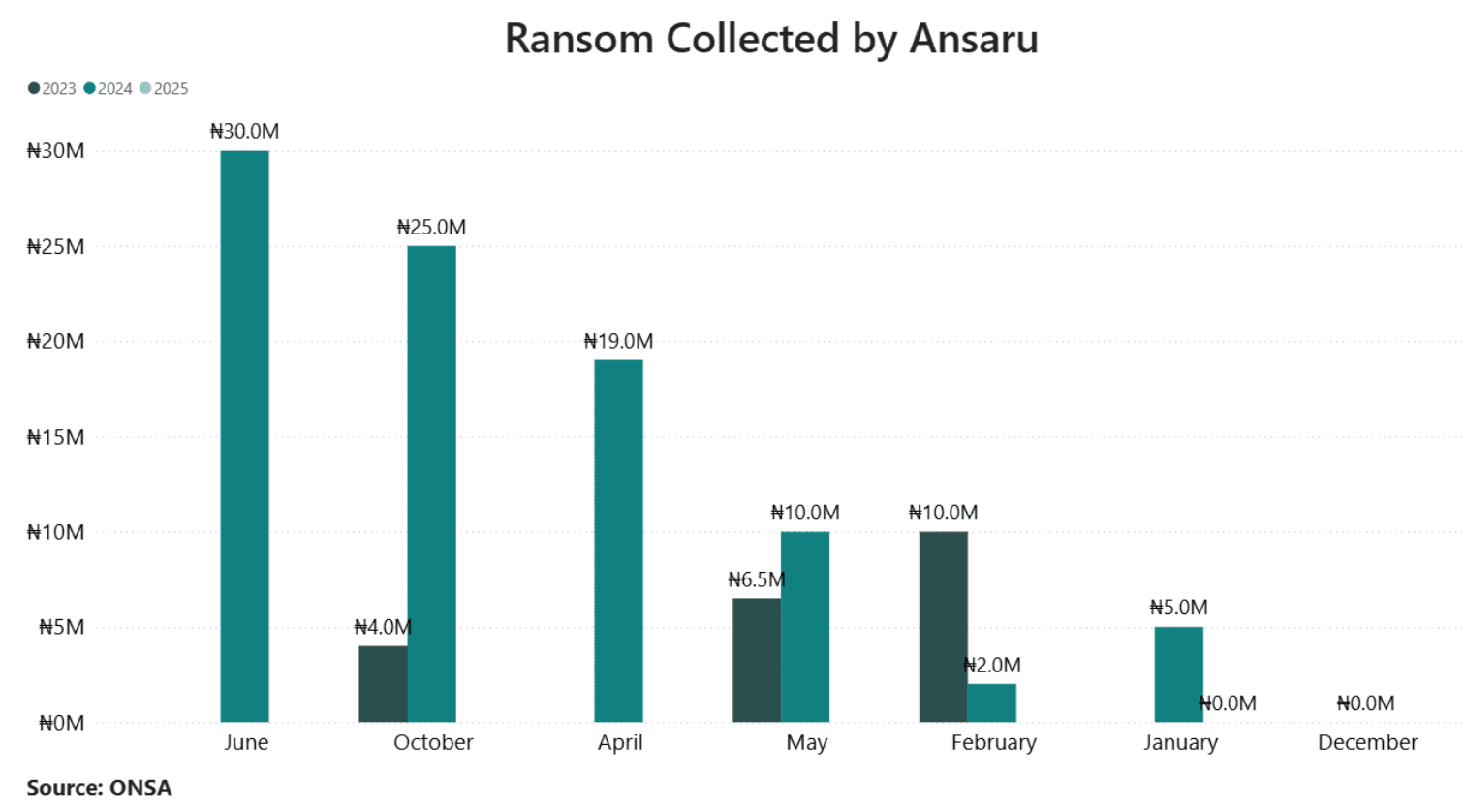
For Ansaru, the cumulative effect has been devastating. Once a disciplined al-Qaeda affiliate with operational depth across the Northwest and the Kainji–Borgou corridor, it now faces a leadership vacuum, defections, and factional splits. Sources reported fighters are drifting toward ISWAP, whose organizational model and ideology are more compatible with what remains of Ansaru's leadership. Reports of an Ansaru–JAS alignment persist, but longstanding doctrinal differences make such a union fragile. The greater risk lies in an ISWAP absorption, which would likely mean more professionalised attacks on military and security infrastructure.
What to watch next is whether Nigeria sustains the tempo. The decisive lever isn't only leadership arrests—it is the systematic targeting of financial and logistics chains. Court records linking illegal mining to terror finance suggest future prosecutions and intelligence should extend to mining activities, local buyers, haulage firms, and cash couriers. Defection flows into ISWAP should also be monitored closely, as they will shape whether violence tilts toward harder military targets. And in Nigeria's porous tri-border with Niger and Benin, HUMINT indicators—fuel smuggling, ammunition pricing, and satellite handset traffic—often surface weeks before operational surges.
Argon Open-Source Monitoring confirms that leadership losses typically produce brief lulls in violence, followed by fast realignments as groups re-bundle and probe new routes. Those are the moments when intelligence wins can be converted into durable degradation—if the pressure on money, logistics, and networks is maintained.
At its core, Nigeria's counterterrorism doctrine has entered a new phase. By fusing HUMINT, OSINT, and covert operations into a unified playbook, Nigeria is not just chasing insurgents—it is rewriting the battlefield rules. Quiet decapitations, financial disruption, and intelligence exploitation are leaving militants scrambling in the shadows.
Similar Insights:
Loading similar insights...
